Cyber Mapping – One of the tenets of risk tolerance is considering the fallout of something going wrong. The risk may originate as a technical one, but for CISOs the challenge is deciphering the organization’s . The scope now goes beyond a simple smash and grab to Ransomware attackers that take weeks or months mapping the infrastructure and analysing tools and work-from-anywhere notion. Evolving Your .
Cyber Mapping
Source : carnegieendowment.org
Mapping the cyber security capacity building network: it just got
Source : cybercapacity.org
Mapping the Cyber Terrain: The Indispensable Role of Network
Source : www.linkedin.com
JRC Publications Repository Cyber Resilience Act Requirements
Source : publications.jrc.ec.europa.eu
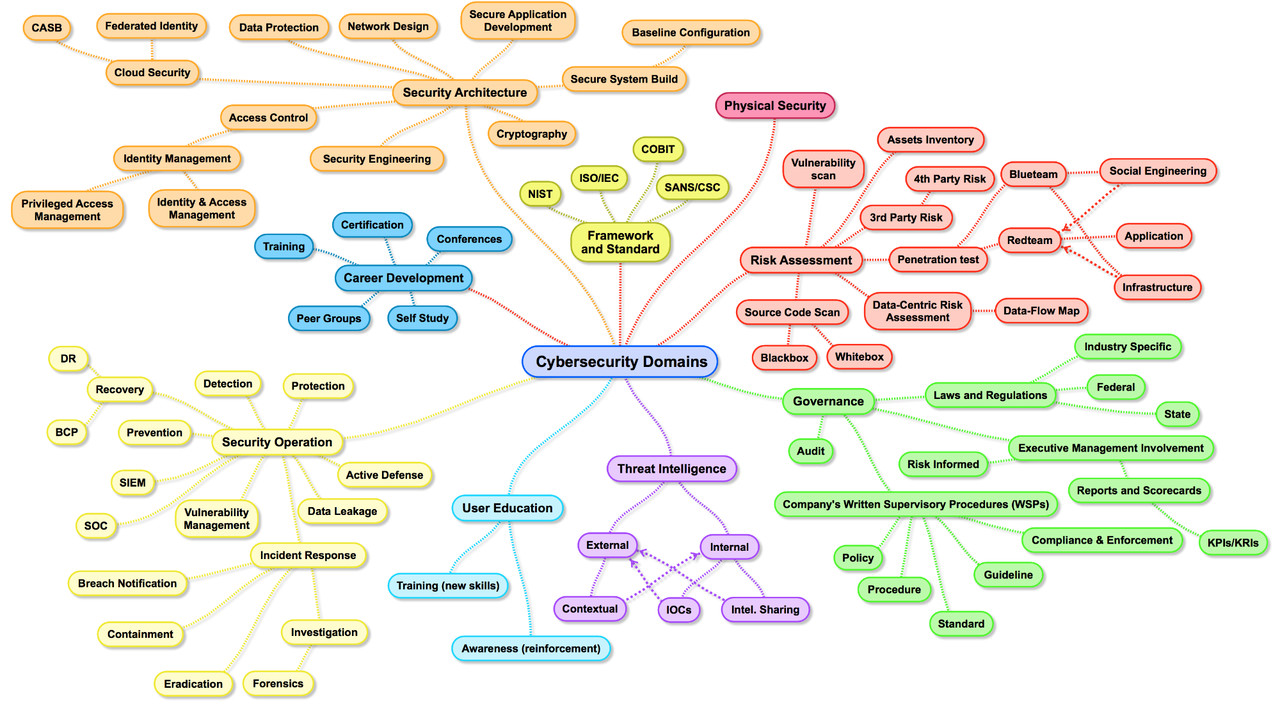
The Map of Cybersecurity Domains (version 2.0)
Source : www.linkedin.com
Mind Mapping & Cybersecurity SimpleMind
Source : simplemind.eu
Mapping of the external Cyber Capacity Building projects funded by
Source : www.eucybernet.eu
Cybersecurity Domain Map ver 3.0
Source : www.linkedin.com
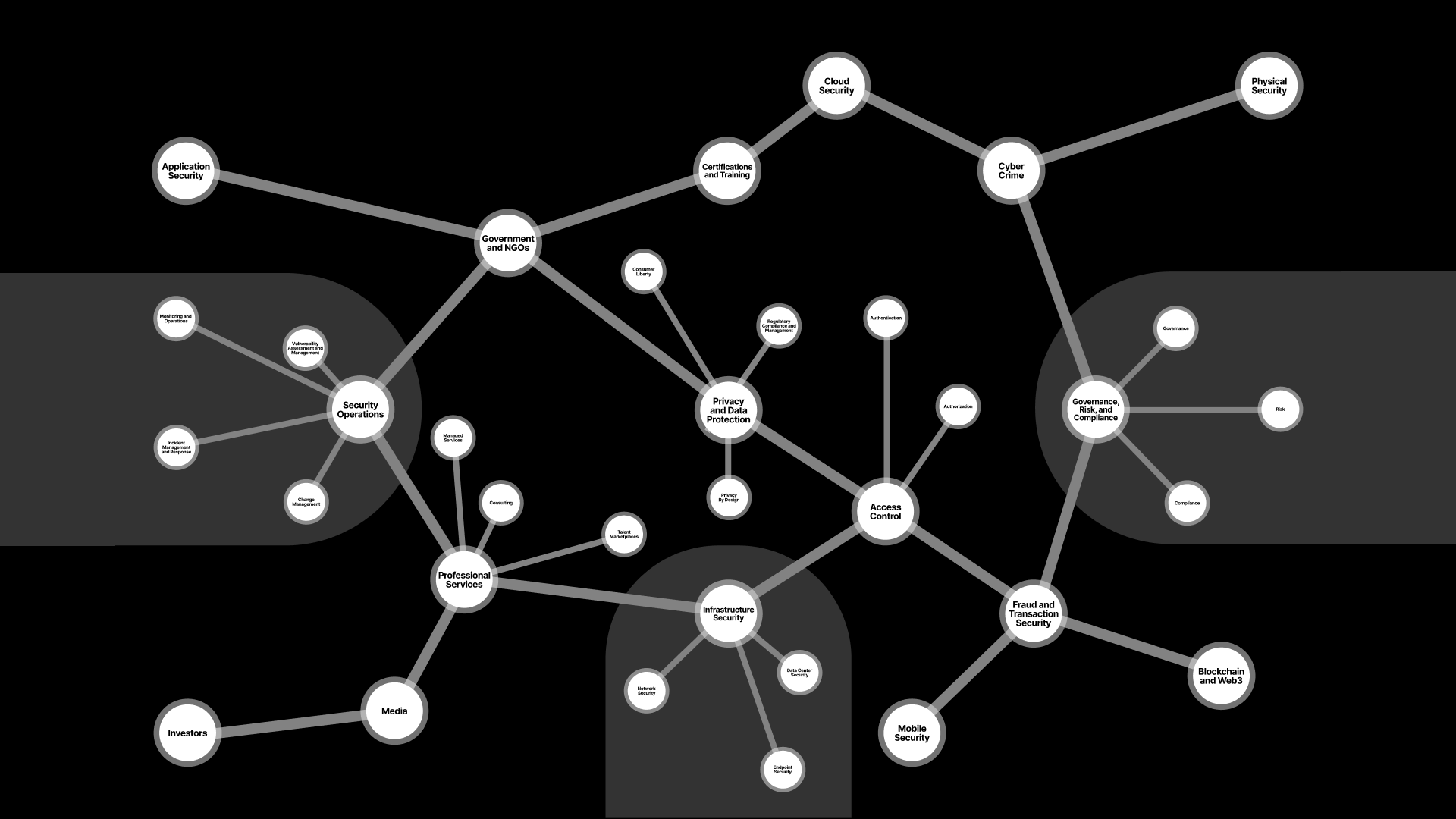
Mapping the Cybersecurity Ecosystem
Source : strategyofsecurity.com
Cybersecurity Made in Europe Mapping the European Cybersecurity
Source : european-champions.org
Cyber Mapping Cyber Mapping the Financial System Carnegie Endowment for : Discover six top cybersecurity internships for summer 2025. Gain valuable experience and enhance your skills in a rapidly evolving field. Apply now! . In today’s digital landscape, cybersecurity has become an essential pillar of organizational resilience and operational integrity. The sophistication and frequency of cyber threats continue to .